No activity on the Internet remains unnoticed. When we search for information, send emails, visit websites, shop online, and message in social networks, all of these actions leave traces. With this information, it is easy enough to find out most of a user’s sensitive data. And there is no way to completely hide your presence on the Internet – it’s physically impossible! However, there are certain tools through which you can greatly complicate the process of collecting information about you from the Internet, making it unprofitable for intruders and other “collectors” of confidential information. In this article, we will share some practical tips on how to be anonymous online.

Before selecting the tools to hide your activities on the network, you should clarify why you want to be anonymous and from whom you want to protect your online activity. Here is a list of the main “collectors” of your confidential data:
- Internet Service Providers (ISP)
ISPs collect marketing information about their customers (preferences) to sell it to various corporations. In addition, in some countries, ISPs are legally required to keep all data on the Internet activity of their customers and show it to government agencies if they require it.
- Search Engines
Google, Yahoo, Bing, Baidu and other search engines all collect marketing data for their subsequent sales. In addition, they use this information for personal gain, for example for research and loyalties.
- Hackers
In 98% of cases, hackers need the financial information to steal money. So, the following tips for safe online shopping is especially important for preventing identity theft in the future.
- Government
Many modern states, even the democratic ones, collect information about their citizens to strengthen their political power.
- Corporations
A marketing department of any company needs data about the Internet users, which is used to analyze the customer needs and habits, and to learn how to sell more products to them.
If you want to protect your personal data, you don’t have to stop using the Internet. You can employ some tricks that will help you to stay anonymous on the network and hide your online activity.

Private Browser Modes
The leading Internet browsers (Safari, Chrome, Mozilla Firefox, Opera, and others) provide the incognito mode option. When you use this mode, the browser doesn’t collect a list of visited sites, logs and your search history. Also, it deletes all cookies, temporary files and data entered in the registration forms as soon as you close the window or the tab. The only things that can remain are the bookmarks and downloaded files. This mode also disables the installed browser extensions that require the user’s personal data.
The advantage of incognito mode in browsers is that no additional software installations and knowledge are needed. The main disadvantage is the lack of clarification about the safety of such a connection (there are only general theses in F.A.Q.). In addition, the selected mode can only protect anonymity of the traffic that goes through the browser. All other connections will remain open and unprotected.
There is also another privacy-keeping technology used in some browsers, which is related to the prohibition of monitoring the user activity on the headings of web pages. The Do not track” technology“ is now used in Mozilla Firefox, Google Chrome, Internet Explorer and Safari.
Anonymizers
Anonymizer is a special service where you enter the address of the website you want to visit, and it changes your IP address allowing you to be incognito. The resource you visit saves the logs not of your IP-address but the IP-address of the anonymizer. There are free and paid anonymizers. The advantage of anonymizers is that they don’t require installing additional software. However, they have some disadvantages:
- Your ISP can easily find out which websites you visited.
- Anonymizer does not encrypt your data, so anyone can intercept it.
- The access speed is usually low, and you cannot upload large files.
- There is no guarantee that the anonymizer owner will not transfer information about your IP address at the first request of any interested person.
- If you use free anonymizers, you will likely have to view ads.
- In free anonymizers, you cannot select the IP address, as it replaces your IP address automatically.
Proxy
A Proxy is a service that allows you to visit a website through an intermediate proxy service. This provides anonymity by substituting the visitor’s IP address. Depending on the degree of security, there are some types of Proxy servers:
- HTTP-servers (usual) – pass only HTTP-traffic through themselves.
- SOCKS-servers – pass any traffic through themselves.
Proxy servers help to maintain anonymity in order to bypass various regional restrictions and provide basic security for your confidential information. This is useful if you want to remain anonymous for search engines, corporations and Internet intruders.
Pros
- ✓ Availability
- ✓ Price (there are free servers as well)
Cons
- 𐄂 Proxy protocols do not support traffic encryption
- 𐄂 You have to find a Proxy-service you can trust
- 𐄂 You must constantly filter traffic for HTTP servers
- 𐄂 You need to set up a configuration for each new application or install a special software
Tor Browser
TOR (Onion Router) is a browser with an open source software, which uses a layered router system. This creates an anonymous connection between your computer and the web resource with protection from “wiretapping.” It does not collect logs, does not transmit any information about the user to the Internet, and applies a two-way TLS connection.
Pros
- ✓ If all the rules are followed, the traffic sent from your device will be maximally anonymous
- ✓ Simplicity – download, launch and use it
Cons
- 𐄂 A low connection speed
- 𐄂 The traffic which is originating from the opposite side is not encrypted
Virtual Private Network
A VPN is a technology of a secure connection between your device and the internet network. creating the most anonymous channel. This channel is called a VPN tunnel where all the traffic is encrypted, so no one y can intercept the data. This forms a shield of protection from hackers, government agencies and other persons who may wish to obtain your data.
The main advantage of a VPN is that it provides maximum traffic safety and does not require a long and complicated configuration. The disadvantage is that it can affect on the connection speed.
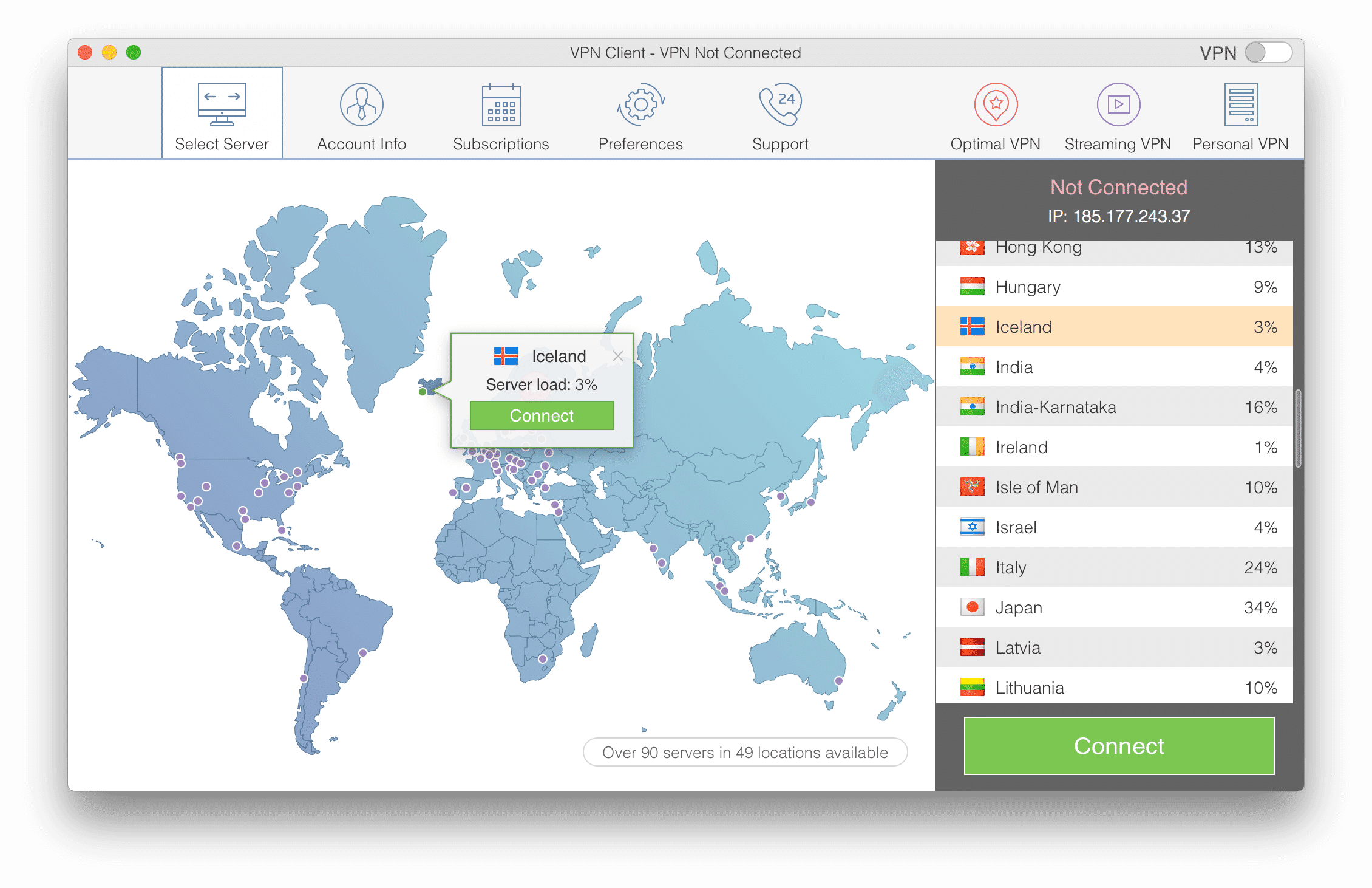
If you want to try a VPN, you can download VPN Client for Mac. This app provides 90+ VPN servers across 40+ countries. Also, It offers a 7-day Free trial with the unlimited VPN and unlimited bandwidth.
A brief list of other solutions that increase the level of your anonymity on the Internet:
- Firewalls
- Steve Gibson’s ShieldsUP! – a program that detects vulnerable or open ports on your system.
- LastPass – a secure password manager.
- Stay Invisible – a service that shows a full report on the information that your browser sends to the Internet.
- Add-ons for browsers that recognize and block ad networks, web analytics tools and links to social networks, and as a result, they are restricting the monitoring of you.
- Comodo Dragon, Comodo IceDragon and Dooble – alternative browsers that, according to developers, do not share your data with Google.
- DuckDuckGo – a search engine that, according to its creators, does not recognize the IP address and does not store the client cookies.
- MyKolab, HushMail – protected email-services.
- Enigmail – a client for Thunderbird, which allows you to encrypt your messages.
- Airmail, GuerrillaMail, and Mailinator are services for creating temporary accounts.
Conclusion
Being anonymous on the Internet doesn’t mean that you have to immediately stop using the Internet. However, it is vital to maximize your own safety with the above-mentioned solutions. Some of them will significantly increase the level of your online anonymity. Other technologies, for example, a VPN, will provide additional security for your data and help you to prevent identity theft, bypass Internet censorship and avoid intrusive advertising.
