According to statistics, 31% of Internet users have suffered from the actions of Internet scammers. Today remote financial instruments and online-banking are enough developed, and people do online shopping or make other online payments regularly. Also, the worldwide scandal about Facebook’s leakage of information does not cease. This article will tell you how to secure your private data and avoid identity theft.
Contents:
Interesting Fact
Facebook shares fell by $58 billion during one week, and indignant users launched a flash mob under the hashtag #deletefacebook, calling for the removal of their accounts from the social network. Facebook CEO Mark Zuckerberg promised to make the service safer and reduce the amount of information requested from users. But history has already made users think about the digital security of personal data on the World Wide Web.
What is Identity Theft?
Data theft refers to the hacking of an Internet user’s data. A hacker can get access to your data, including account logins, passwords, credit card numbers, and so on. This means that you should pay attention to your identity theft protection. Follow our suggestions to protect your privacy on the Internet.
Online Security Tips
Check website addresses
Perhaps the most common way of fraud on the Internet is phishing – the theft of personal data for subsequent theft of bank cards or Internet wallet data. Websites with free access to paid content are often the source of spyware designed to steal personal information. This allows hackers to obtain a full copy of your information, including a credit card number, even if the databases are encrypted. Oppositely, paid services usually require your data.
To recognize the phishing site and avoid hacking your sensitive data, you should check the web address (domain name) for the correct spelling. If there is one wrong letter in the address, the site is suspicious.
Secure your personal data
The best way to prevent social networks from collecting information about you is to stop using them. If this seems to be impossible for you, please take time to set up the security configurations of your social network accounts. For example, on Facebook, you can prohibit third-party companies to collect your data. For this, go to the Settings page → switch to the Applications and Sites section → delete the apps and sites that request your account information.
Disable cookies
To keep your data private, disable collecting cookies by web pages. In most browsers, cookies can be disabled in the Settings. Another way to avoid leaving digital traces is to use the Incognito mode in the browser. This will not preserve the browsing history and information inscribed on the sites. It’s also worth ignoring banners and pop-ups on sites and suspicious links in e-mail messages.
Think about what you share on social media
The information about hobbies, location, and work schedule can be successfully used, for example, by thieves. That’s why you may want to refrain from sharing photos with geotags from travels after your return.
Do not click advertising links
To maximally secure your information, you should publish minimum information on social networks. Do not click on advertising links and do not take entertainment tests – they also collect information about the users.
Use the software only from trusted sources
Installing suspicious software makes your computer vulnerable to intrusion from outside. These kinds of intrusions are prone to happen when various kinds of games or screensavers are installed. Sites that distribute such software can simultaneously spread viruses through downloads. For example, if you are a Mac user and have a choice to download a particular app from either the App Store or from the web, give preference to the App Store.
Regularly change your password
Make it a habit to regularly change your passwords, and be sure to do this every couple of months.
Use unique passwords for each site
One of the reasons that enable the theft of a user’s information is authorization through an email address and using one password for all accounts. If the same password is used for multiple sites, hacking one site means simultaneously hacking all the other ones. You should create strong passwords for each individual account. To remember passwords, you can use special applications and online services.
Be careful when buying online
Take care of your data, especially when you buy something online. Online stores ask for information such as name, surname, phone number, delivery address, bank card number, and so on. To prevent this information from being used by cybercriminals, firstly, you need to select only proven online trading platforms, and carefully study the reviews about the store before purchasing. You can check the reliability of the site by using special online services, for example, the “Web of Trust.” Check whether the site supports the technology of secure data transmission (in the URL address, you should see HTTPS, not HTTP).
Read also: “How to shop online safely”
Avoid using public Wi-Fi
Try to limit the use of public hotspots. If you use a public network, at least make sure that it belongs to the organization (cafe, restaurant, hotel) which is providing it. In an official public network, trap points may occur. In this case, a user connecting to such a network exposes his data to serious danger. If you still need them, use applications that provide encrypted connections (anonymity on the network). You can use a VPN (Virtual Private Network) service, which encrypts your data sent to the website and makes it almost impossible to hack your data.
Check web address
Whenever possible, and make sure that the web pages you visit are “HTTPS” encrypted. Look at the beginning of the web address you are accessing. If the URL starts with “HTTP,” log out and never enter sensitive data to this page.
Track logins
Keep track of where and when you entered your account. Social networks, mail services and messenger applications can inform you when someone is trying to access your account. If there are no automatic notifications, you can usually see the list of recent sessions (logins to your account) in your account settings and block the ones which seem to be suspicious.
Use two-factor authentication
Install additional protection against unauthorized logging into your accounts. For this, you need to enable two-factor authentication. If you enable this feature, then at the login to your account you will need to enter not only the password but also a one-time code you receive either via SMS or email address. Yes, it’s longer; however, privacy and security on the Internet is more important.
Use VPN
Be anonymous on the network. To do this, you will need to use a VPN (Virtual Private Network). This technology allows you to access Internet resources so that no one knows your real IP address and your current location. This is important if you want to keep your location secret. Generally, a virtual private network is a technology that provides a high level of security of your personal data. And now we are going to highlight how a VPN works and how it can help you in personal data protection.
What is VPN?
VPN is a virtual private network which protects the transmitted data from any external interference. The data is encrypted according to a certain algorithm, which is almost impossible to crack. Instead of the real IP address, each user gets a new virtual IP address so that all services recognize the user according to the assigned VPN geolocation.
How does a VPN work?
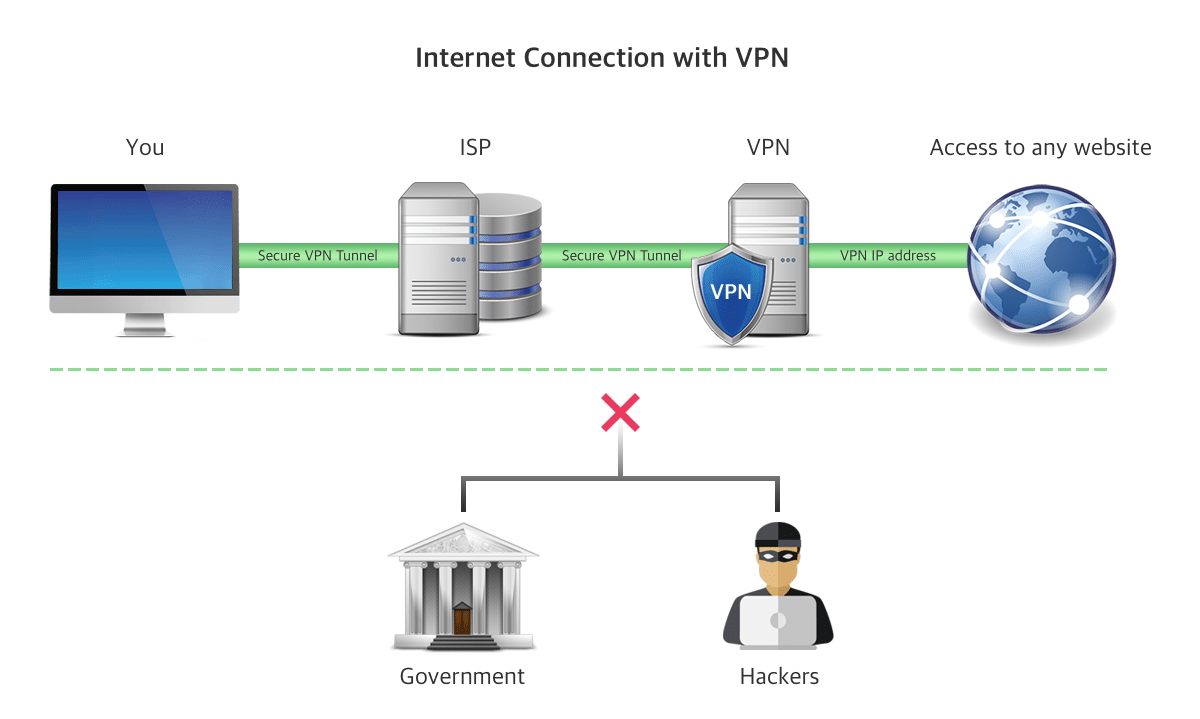
With a standard connection to the Internet, all the data about pages you visit, including some personal documents, can be viewed by your Internet service provider (ISP.) Also, this information can be intercepted by hackers. But if you use a VPN, every time you access the network, it creates a protected VPN tunnel between your computer and the remote server. This forms a shield of protection from hackers, government agencies, and other persons who may wish to inspect your traffic and data.
When using a VPN, you connect to the Internet through a VPN server. Your ISP does not see where you go and what you do on the Internet. The user’s address depends on the selected VPN server. For example, if you are in the USA, you can hide your real IP address and replace it with a virtual address (European, African or Asian IP).
Here is an illustration of how a VPN works.
Which VPN service to use?
When you need to choose a VPN service, you have to approach this task responsibly. In short, the VPN provider should provide a wide list of VPN servers, fast VPN connection speed, no logs policy and the latest technologies of secure encryption of your data.
Given all these parameters, we recommend that you try VPN Client for Mac.
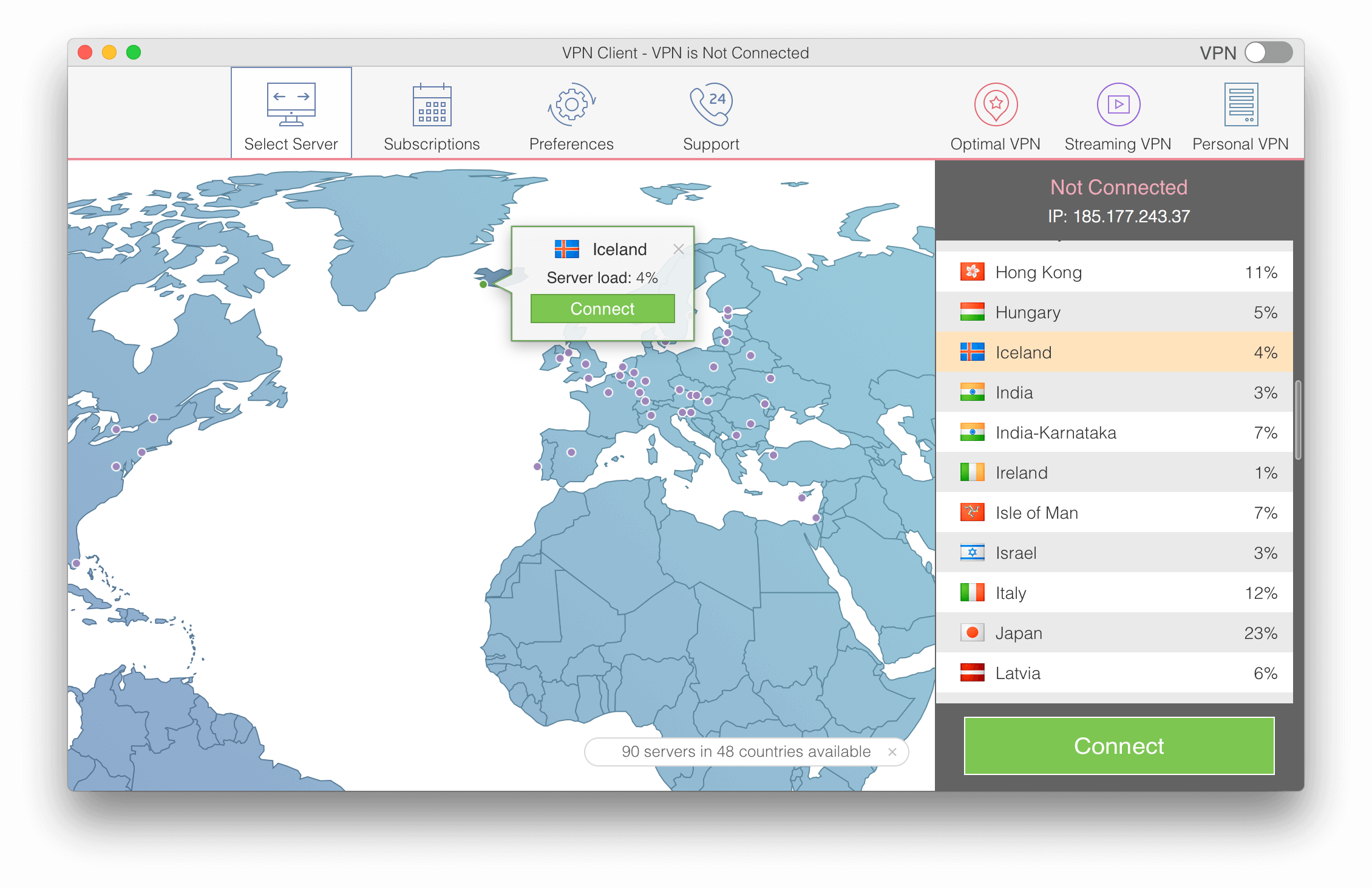
VPN Client provides strong encryption and highly secured protection of your traffic. Download VPN Client from the Mac App Store and get a free 7-day subscription plan.
Conclusion
Your personal data is at risk every day. To briefly summarize our tips, we recommend the following to get the best identity theft protection:
- Check website addresses to avoid fake phishing web addresses.
- Use two-factor authorization on all sites and services.
- Trust only on sites with secure data transmission.
- Use unique passwords for different sites and services.
- Use a VPN, working with open Wi-Fi-points.




